Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Real Time Weapon Detection using YOLOv8 and Alert Mechanism
Authors: Pradyunya Chunchwar, Umesh Shelare, Aastha Nagpure, Rinesh Patil, Dhiraj Dhole, Prof. Rushikesh M. Shete
DOI Link: https://doi.org/10.22214/ijraset.2024.60177
Certificate: View Certificate
Abstract
Security cameras and video surveillance cameras have become an important part of public safety. However, in many cities, these systems still manually detect high-risk situations. Understaffing in security services can lead to delays in detecting incidents or unforeseen threats, putting the public at risk. The aim of this project is to develop a low-cost, effective intelligence-based solution for real-time weapons detection and surveillance video analysis in different situations. As can be seen from many statistics, the incidence of gun and dangerous weapon crimes is increasing every year, making it difficult for the police to solve the problem in time. Crimes caused by guns or knives are very common in many places, especially in places where gun laws do not exist. Early detection of crime is critical to public safety. One way to prevent these situations is to use video surveillance to detect the presence of dangerous weapons such as guns and knives. Monitoring and control now also require monitoring and intervention. Here, we present in video a system for tracking weapons suitable for tracking and controlling targets. We use the YOLOv8 (look once) algorithm to detect weapons in live video. YOLO model is an end-to-end deep learning model; it is very popular because it is fast and accurate. Previous methods such as region-based convolutional neural networks (R-CNN) required thousands of network tests to make predictions for an image, which could be time-consuming-Optimization is a laborious and painful process. He focuses on specific areas of painting and trains everything personally. The YOLO model, on the other hand, passes the image through the neural network only once. Since speed is important in real-time video, we use the YOLOv8 algorithm. This data was trained to classify three groups of weapons (pistols, knives, and artillery). When a weapon is detected, an alert is sent to authorities who can take action and reduce crime before it becomes a crime. Powered by Tensorflow, the system took 294 seconds in the first test to identify weapon types in 9 categories.
Introduction
I. INTRODUCTION
Microscopy was performed on a desktop computer equipped with special equipment to ensure proper viewing. This study aims at improving the frame size obtained from video analysis, which is an important technique that can be effective in video analysis Analysis focuses on different dimensions and the results show windows the most effective size for this important task is 50, which is ideal Highlights the importance of index-scaling to achieve results. Then move on to the research phase, such as mean accuracy (MAP) and true accuracy testing. More importantly, confirming the ability to calculate the accuracy and quality that is important in the analysis application The ultimate litmus test of the model is its ability to detect weapons illustrated and described. The YOLO (You Only See One) example reviewed here shows that it has the ability to detect and disperse weapons. This potential incident has significant safety and public safety implications, and rapid and accurate detection of these events is critical.
A. Optimizing Railway Surveillance with CivicWatch: AI-CCTV Synergy
Advanced-A.I. CivicWatch, an innovative solution introduced to address the challenges faced by the Indian Railways, uses sophisticated artificial intelligence (AI) and machine learning (ML) techniques to transform passenger safety, operational efficiency and safety measures Civic Watch’s main strength is its ability to analyse real- time data from CCTV feeds using AI algorithms. Using sophisticated computer vision techniques, CivicWatch can quickly identify abnormalities in passenger behaviour, identify potential safety risks, and accurately monitor business processes This real- time analytics enables construction stop early, enabling railway authorities to react quickly to emerging situations and prevent premature incidents they escalate
Additionally, the predictive capabilities of the Machine Learning algorithms built into CivicWatch provide valuable insights into resource allocation and operational patterns By analysing historical data and patterns, CivicWatch is able to forecast passenger a predicting throughput, increasing times, and optimizing staffing levels accordingly. This proactive approach not only enhances the passenger experience by reducing overcrowding and wait times but also improves operational efficiency through streamlined infrastructure management
In addition, CivicWatch plays an important role in crime prevention and investigation at railway universities. Advanced AI algorithms can accurately identify suspicious activities, unauthorized content and potential security breaches, enabling security personnel to intervene quickly and mitigate risks Such security management this not only prevents crime but also increases passenger confidence in the safety and security of railway infrastructure.
Overall, the seamless integration of AI and CCTV technology through CivicWatch represents a turning point in rail monitoring and management. Leveraging the power of advanced AI systems and predictive analytics, CivicWatch empowers rail authorities to proactively address challenges, improve efficiency, and ensure a safe and efficient travel experience travellers.
B. "YOLOv8: Real-time object detection and tracking in CCTV surveillance
The YOLOv8 algorithm is an integral part of modern computer systems, especially in time-consuming asset tracking and CCTV surveillance and monitoring. This tool explains how YOLOv8 works in this section and videos are periodically shown to capture video presentations for better understanding.
- Video Insert
The heart of YOLOv8 is its ability to seamlessly integrate with the web. CCTV cameras are always used as an accessory. accepts streams of video data.This data stream forms the basis of the algorithm’s operations, enabling it to analyze and capture objects in a timely manner.
2. Pre-processing Frames
Once each frame is acquired from the video stream, YOLOv8 starts the pre-processing step. These include changing the standard resolution of the frame, normalizing the pixel values to ensure consistency, changing the input model and compatibility as required by the model From this preprocessing the algorithm prepares the input data for later processing and analysis . . . .
3. Meshing and Feature Extraction
After preprocessing, YOLOv8 further classifies each. Frame the grid cell. This web-based approach facilitates optimal results by assigning specific areas of the frame to the brain. Relevant information such as edges, textures, and wing colors were then retrieved by feature extraction on each grid. This feature extraction step forms the basis for subsequent object recognition and classification tasks.
4. Bounding Box Prediction
One of the key features of YOLOv8 is its ability to predict that bounding boxes will yield known features in each cell. These bounding boxes contain important information about the detected area, including its position (x, y), shape (width, height), and a confidence score for the number of objects in the box around.
5. Object Classification and Reliability
Analogous to bounding box prediction, YOLOv8 classifies objects by assigning a logical class to each object. Using predefined objects (e.g. people, cars, guns), the algorithm finds the probability of objects occurring in each category. This class result, together with the confidence score obtained from the prediction box, indicates the ability of the algorithm to detect the object.
6. Threshold filtering and non-maximum suppression (NMS)
To obtain the distribution and reliability of the scores, YOLOv8 uses threshold filtering to refine its findings. By changing the confidence level and possible classes for the bounding box, the algorithm excludes low confidence levels and increases the confidence level of its output Furthermore, YOLOv8 sets a non-bounding maximum number (NMS) method is used to solve redundancy and overlap problems in bounding box calculations. This algorithm from NMS was chosen to preserve the most reliable identification by minimizing re- guessing, thus improving the accuracy and efficiency of target identification
7. Output Visualization and Tracking
Finally, YOLOv8 is a multi-visual toolset that incorporates models with image concepts, class names, and confidence scores. This visual mapping provides immediate feedback on the algorithm’s recognition capabilities, allowing users to track and interpret visual objects.
In addition, YOLOv8 and better object discovery algorithms can be added to facilitate continuous analysis and tracking of objects from sequences. By monitoring the object as it moves, the algorithm improves the accuracy and value of the analysis results, giving the user a better understanding of the nature of the situation
In summary, YOLOv8 embodies a state-of-the-art approach to real-time object tracking and monitoring in a state-of-the-art CCTV that monitors the environment. YOLOv8 provides powerful and efficient for many tracking applications thanks to its processing methods that include pre-processing, grid-based analysis, bounding box estimation, distribution and post-processing. By leveraging advanced computer vision algorithms and leveraging the synergy of the input video stream and the monitoring process, YOLOv8 becomes the foundation of intelligent monitoring systems, contributing to public safety, security and business efficiency. "
II. LITERATURE REVIEWS
Shidik , G.F. , Noerssonko , E. , Nugraha , A. , Andono , P.N. , Jumanto , J. , and Kusuma , E.J. [1] conducted a systematic review of intelligent video surveillance systems from 2010 to 2019. They identified a lack of quality research in the field and aimed to fill this gap through strategies, tactics and analyzing challenges Their study focused on English language journals which follow a systematic literature review (SLR) approach. They have become increasingly interested in video analytics, have identified key applications in various industries, and have published three main concepts: visual analytics, intelligent monitoring and classification, communication and modeling. and data-set" in Shidik, G.F., Noerssongko, E., Nugraha, A., Andono, P.N., Jumanto, J., and Kusuma, E.J. , provide valuable insights for researchers and practitioners in the field, of the present situation and future challenges.
Ninoria , S. , Upadhyay , R. , Philip , R.S. , Dwivedi, R. , Michael , G. , Gupta , A. , & Mishra , S. Ambiguous functions in an academic environment . It uses technologies like CNN, RNN and LSTM to detect abnormal behavior in CCTV footage. The program offers a holistic approach including crime prediction, real-time analytics, anomaly detection, forensic analysis, and social media monitoring. It emphasizes ethical standards, data privacy, and impartiality in the use of Aabased systems. This research helps enhance public safety and law enforcement capabilities through intelligent video surveillance.
JEONG SEO AND HYE YOUTH PARK [3] suggesting that a Framework display at minimum resolution Diagrams by studying two deep tissues together networks: Networks proposed for image enhancement It tries to optimize images with very low resolution Use of dynamic and informative graphics Synthesis of learning cues from object recognition network.. It also uses the results of the image Enhancement network to enhance the quality of enhanced learning data Recognition performance on objects of very small dimensions.
Harsh Jain et. al[4] proposed a use a gun (or) an automatic weapon Search using based convolution neural network (CNN). SSD and Faster RCNN configurations. which has been proposed The program uses two data types. A data structure, a. The former consisted of graffiti, the latter, . which is written by hand. The results are tabulated, both The algorithms have good accuracy, but the implementation itself The conditions may depend on the speed of transactions and accuracy.Much research effort has been devoted to developing real- time weapon detection systems using a variety of algorithms and techniques. One prominent approach is to integrate YOLO and other deep learning algorithms into surveillance systems to better detect weapons and prevent threats.
Previous studies have investigated the use of convolutional neural networks (CNNs) for weapon detection, but their effectiveness in real-time scenarios has been limited due to computational limitations YOLO algorithms, especially YOLOv8, have emerged as a solution it holds promise for real- time detection including weapons in video surveillance
Chen and others.[5] proposed the use of YOLOv3 in real-time weapons detection, demonstrating its effectiveness in identifying firearms and knives in CCTV images. Their study highlighted the importance of optimizing model parameters and preprocessing techniques to achieve high detection accuracy.
Similarly, Zhang et al. [6] developed a YOLO-based weapon detection system that can identify firearms and knives in real-time video. Their research focused on fine-tuning the YOLOv8 algorithm to improve performance under different lighting conditions and camera angles.
In addition to academic research, several commercial solutions have been introduced for real- time weapon detection and management.
III. PROPOSED METHODOLOGY
In this research, we propose a methodology for developing a real-time weapon detection system using machine learning and implementing an alert mechanism for timely notification of potential security threats. Initially, we collect a dataset comprising images and corresponding annotations specifically tailored for weapon detection. This dataset is pre-processed and augmented as necessary using platforms like Roboflow.
We then proceed to train the YOLOv8 model, a state-of-the- art object detection architecture, on this dataset. The model is fine-tuned and validated using standard evaluation metrics such as precision, recall, and mean Average Precision (MAP). Next, we develop a user-friendly interface using Streamlit, allowing users to input images, videos, YouTube URLs, or live webcam feeds for real-time weapon detection. The trained YOLOv8 model is integrated into this application, enabling users to set a confidence score threshold for detection. Additionally, we implement an alert mechanism specifically for live webcam input. Upon detecting a weapon in the live webcam feed, the system generates an alert and sends a security alert email to a specified email address using the smtplib library in Python. This email includes relevant information such as the timestamp and location of the detection for further action by security personnel. Subsequently, we conduct extensive testing and evaluation of the application and model performance, ensuring functionality, usability, and effectiveness of the alert mechanism in timely detection and notification of security threats. Once validated, the system is deployed on a suitable platform, either cloud services or on- premise servers, ensuring scalability and reliability for real-world usage scenarios.
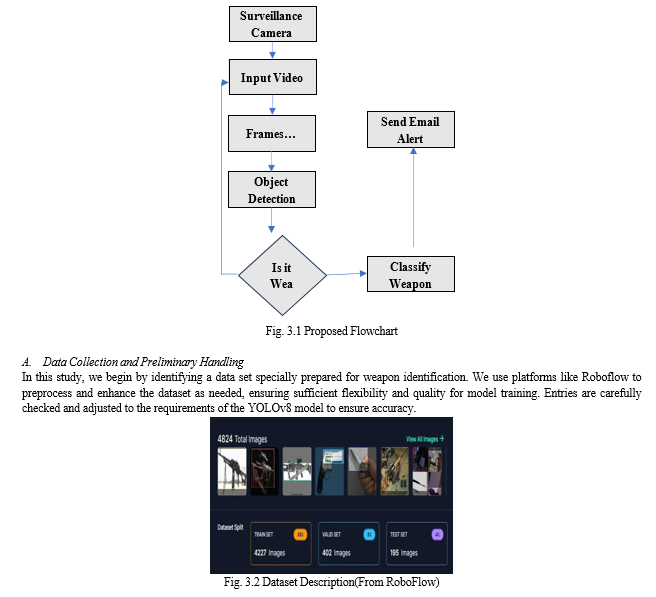

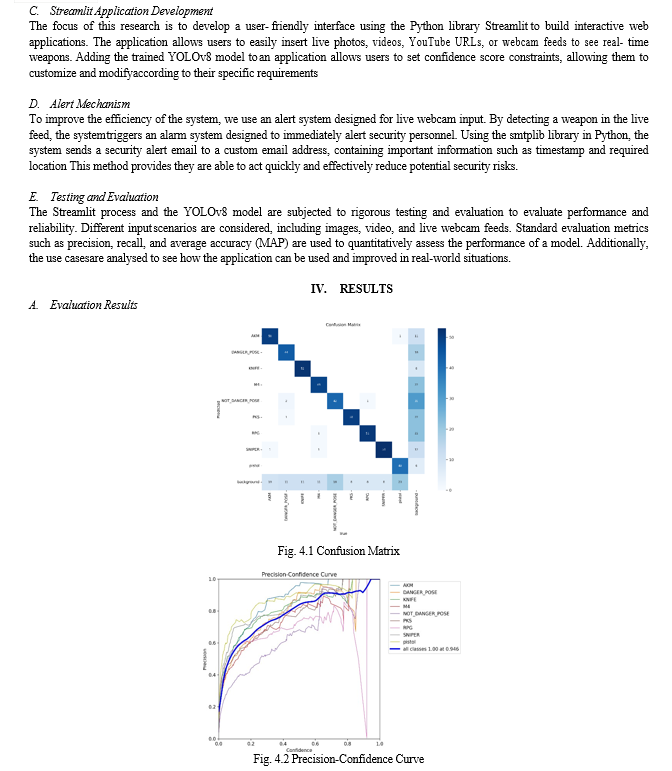
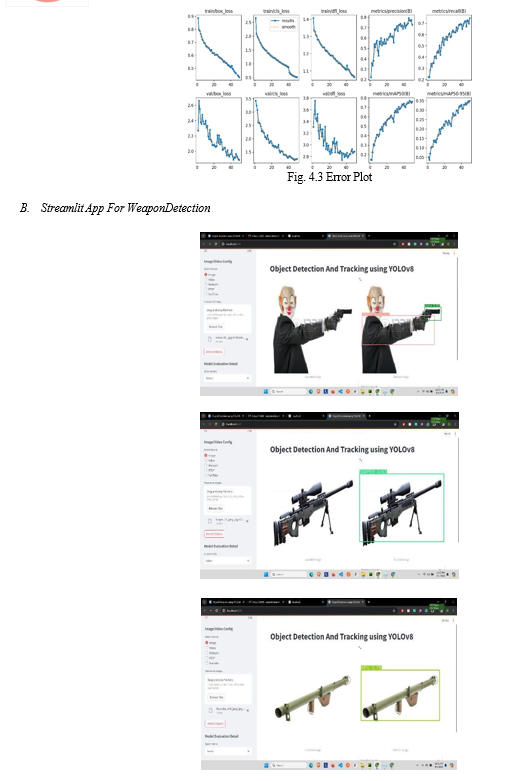
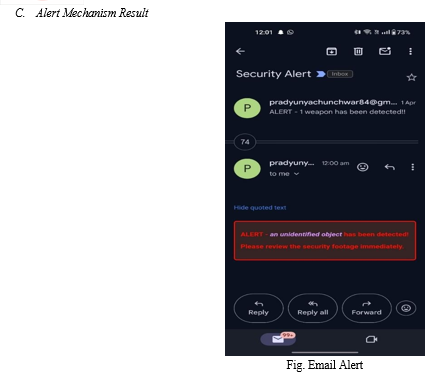
Conclusion
In conclusion, this research project has successfully demonstrated the development of its real-time armed detection system using YOLOv8 for object detection, Streamlit for user interface, and email alert mechanism for timely notification in by careful dataset curation and training examples on custom datasets Through YOLOv8 models have been optimized to achieve high accuracy and reliability in weapon recognition in real-world scenarios The addition of Streamlit made it possible ease of use was facilitated, with images, video, YouTube URL, live for real-time visibility The webcam feed also provides seamless input Furthermore, the email alert mechanism implemented for the users of the system increased by immediately notifying security personnel when weapons are detected in the live webcam feed Notably, the achieved Mean Average Precision (MAP) of 0.78. It highlights the effectiveness of the YOLOv8 model in accurately detecting weapons. This study highlights the importance of using machine learning and deep learning techniques to enhance security measures in public spaces. Going forward, improvements and modifications can be sought to improve system efficiency, efficiency and adaptability to different environmental conditions and safety challenges Overall, this study is helpful advance surveillance and security technologies, and pave the way for more efficient approaches to public safety surveillance and protection works out. The investigate too gives a guide for future considers inside the field of fraud detection and avoidance in online payment systems.
References
[1] Kong, L., Wang, J., & Zhao, P. (2022, May 27). A Lightweight Network Model for Improving the Performance of Military Targets Detection. IEEE, 10(2022). [2] Ruiz-Santaquiteria, J., Álvarez-García, J. A., Velasco-Mata, A., Vallez, N., & Deniz, O. (2021, August 15). Handgun Detection Using Combined Human Pose and Weapon Appearance. IEEE Access, 9(2021). [3] Zhao, L., & Li, S. (2020, March 24). Object Detection Algorithm Based on Improved YOLOv3. Electronics. Retrieved from www.mdpi.com/journal/electronics [4] R. Xu, H. Lin, K. Lu, L. Cao, and Y. Liu, “A forest fire detection system based on ensemble learning,” Forests, vol. 12, no. 2, p. 217, 2021 [5] G. F. Shidik, E. Noersasongko, A. Nugraha, P. N. Andono, J. Jumanto, and E. J. Kusuma, “A systematic review of intelligence video surveillance: Trends, techniques, frameworks, and datasets,” IEEE Access, vol. 7, no. 1, pp. 457–473, 2019. [6] Ya Wang, Tianlong Bao, Chunhui Ding, and Ming Zhu, “Face recognition in real world surveillance videos with deep learning method,” in Proceedings of the IEEE International Conference on Image, Vision and Computing (ICIVC), 2017, pp. 239– 243.
Copyright
Copyright © 2024 Pradyunya Chunchwar, Umesh Shelare, Aastha Nagpure, Rinesh Patil, Dhiraj Dhole, Prof. Rushikesh M. Shete. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET60177
Publish Date : 2024-04-11
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

